2021/09/01 -
CTF
,
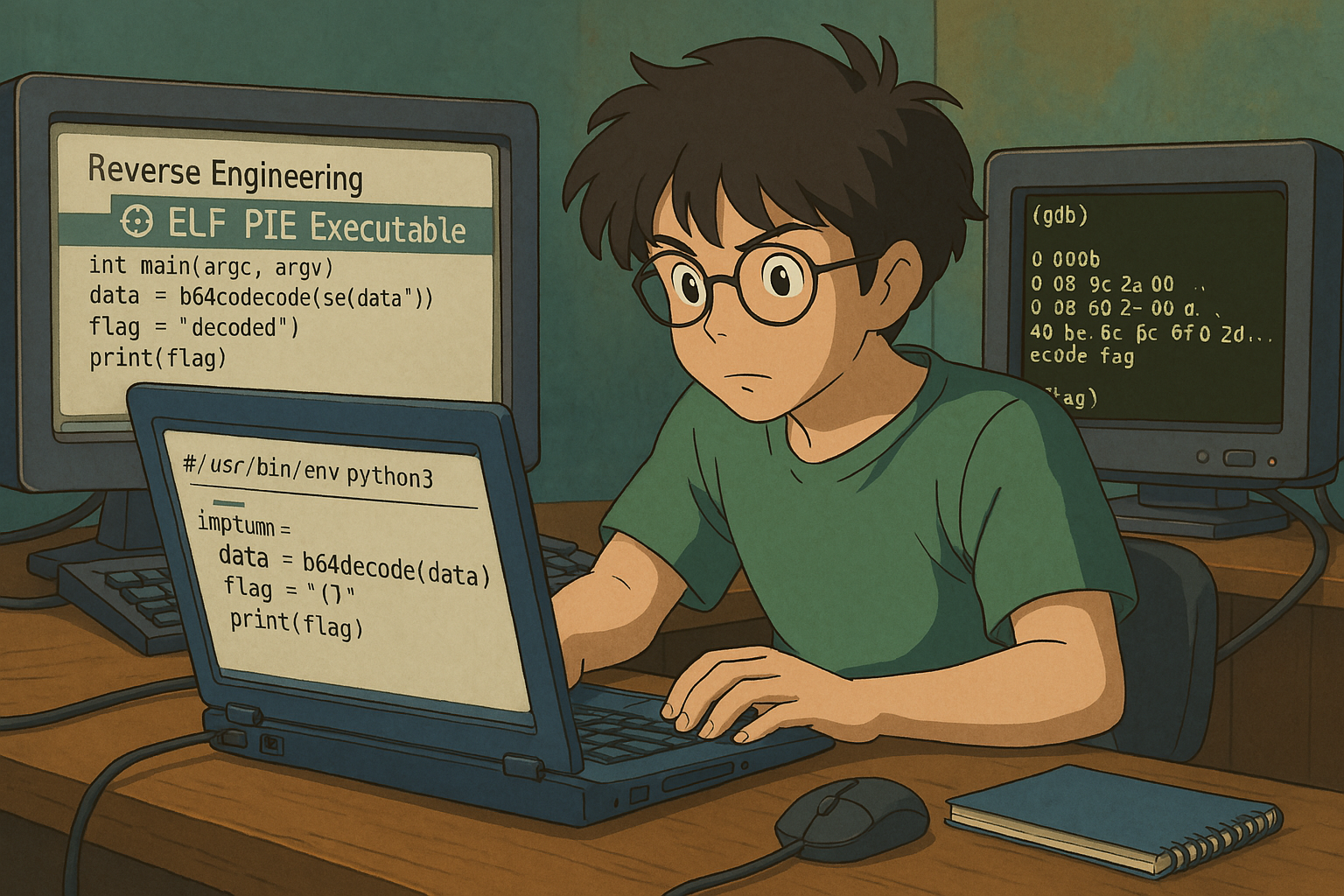
Reverse Engineering
The challenge involved reverse-engineering a compiled 64-bit ELF PIE executable to extract an encoded flag hidden in memory.

2021/09/01 -
CTF
,
Reverse Engineering
The challenge involved reverse-engineering a compiled 64-bit ELF PIE executable to extract an encoded flag hidden in memory.

For this challenge as the description tells us, we should “Win an unwinnable game to receive the flag!” And it also says, “The developer has left in some bugs!”

2021/06/12 -
CTF
,
Reverse Engineering
For this challenge we can download a compiled C file called "crackme2_1.out". When I execute the file, a simple addition of 3 numbers, randomly generate, is required to ...

For this challenge we can download an image called "zipper_1_.jpg". I immediately think that might be probably a steganography challenge (Art of hiding data in image).

2021/06/06 -
CTF
,
Reverse Engineering
For this challenge we can download a compiled C file called "crackme1_1.out". When I execute the file, a password seems to be required to retrieve the flag.