Crack Me 2 - Reverse Engineering Challenge
For this challenge we can download a compiled C file called "crackme2_1.out". When I execute the file, a simple addition of 3 numbers, randomly generate, is required to get the flag. The problem is that we only have 1 second to complete and enter the right result... This is just impossible! I started like the Crack Me 1 challenge and used the command "strings" to display the hard-coded text variables but it was unsuccessful.
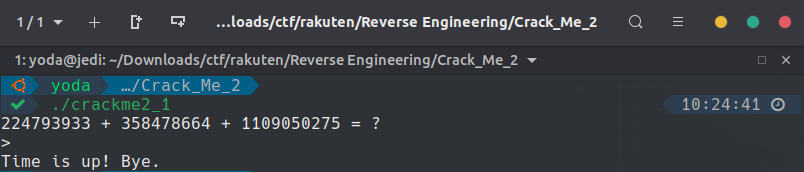
So, I've decided to decompile the program using the tool Ghidra.
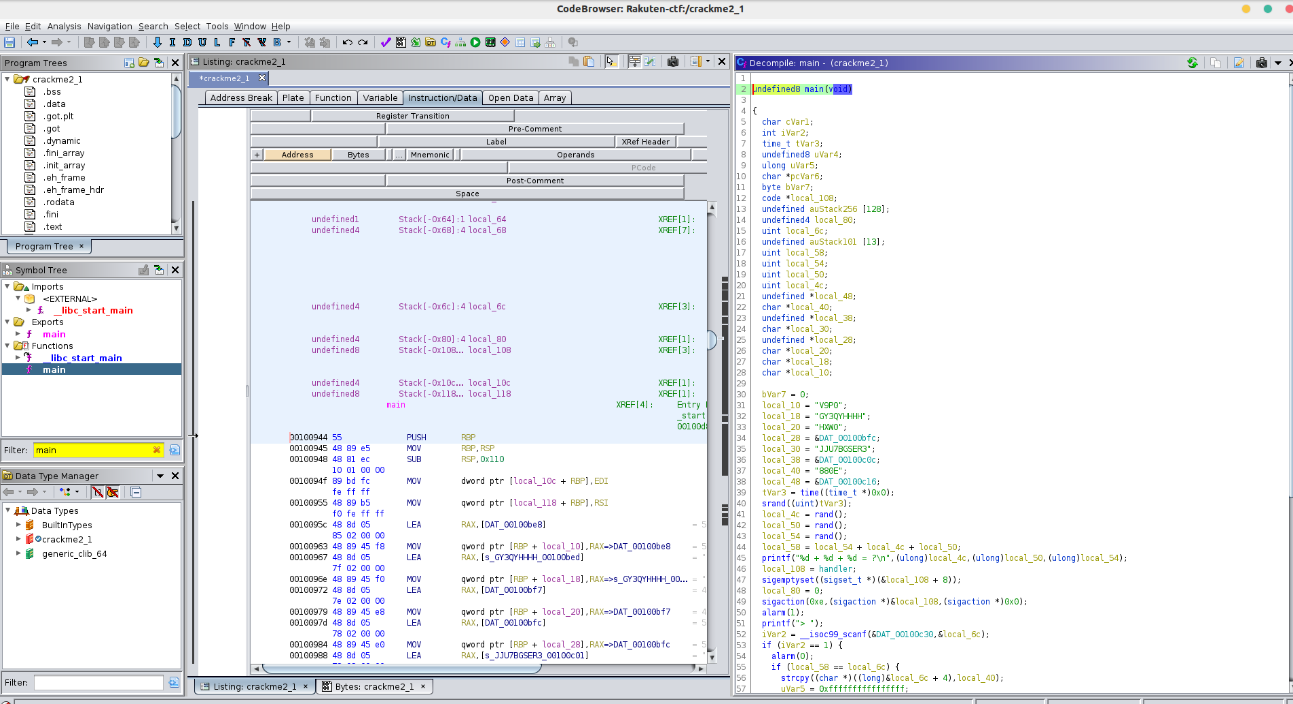
The first thing to do, is to find the main function because this is where the program starts when executed. And I noticed that there is a timer of one second just before be asking for the result.
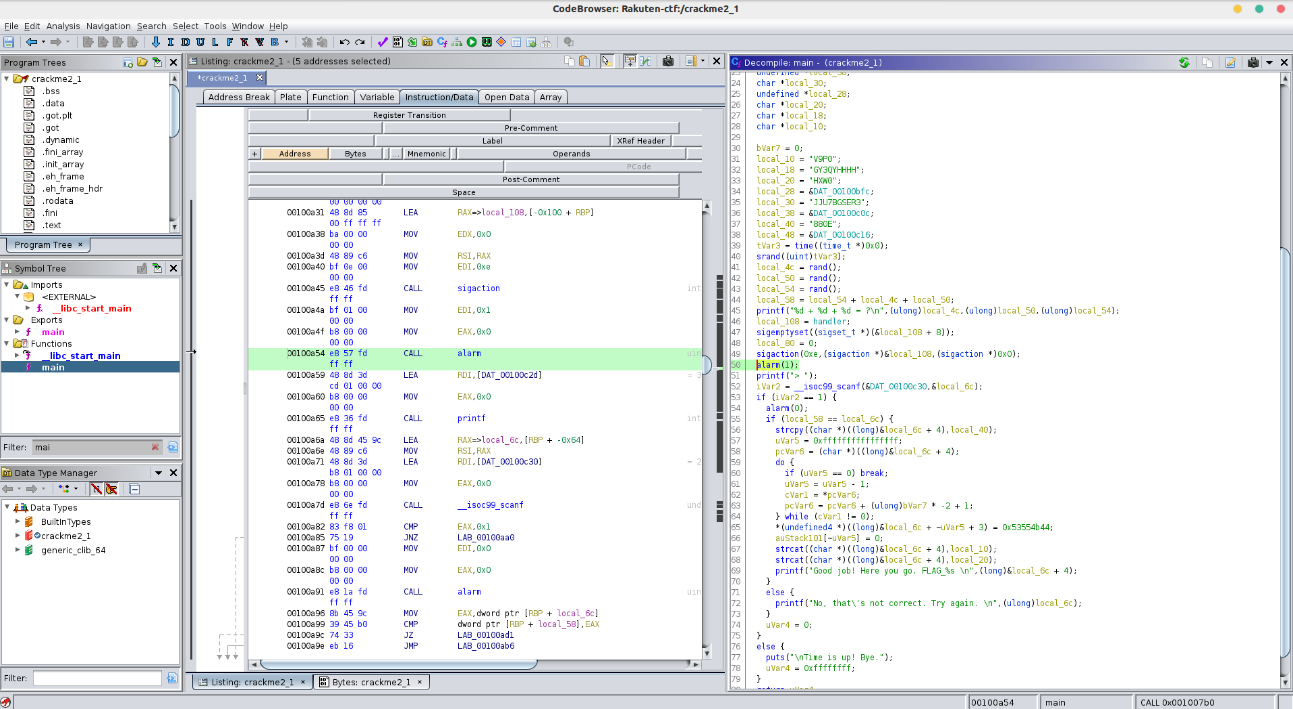
Then, I had the idea to modify the binary value contained in the “alarm” function, in order to have more time to solve the calculation.
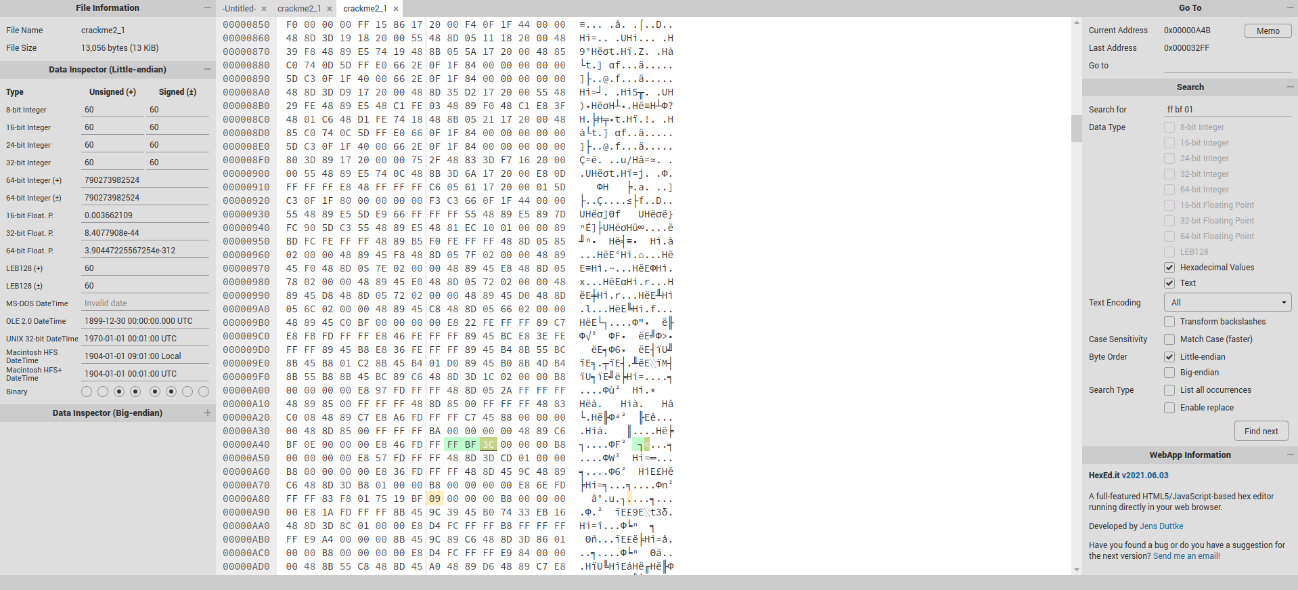
After opening the program in a hexadecimal editor, I precisely identified the line which called the alarm function in hexadecimal.
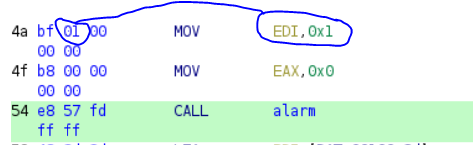
But what I want, is to change the value inside in the alarm function. To do this, we have to see two lines above, where the timer value is set. "bf 01", 01 represents the delay of one second, so I replaced this value by "3C" which corresponds to 60 seconds. This should give me more time to solve the calculation.
Now let's execute the new patched crackme.
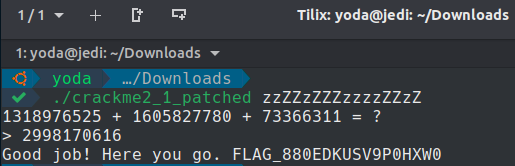
And... Yay, it worked perfectly!